Security Standards & Guidelines
The foundation of application security is security requirements. In many cases, existing requirements are incomplete or inapplicable though. As a result, they are often ignored by the organization (e.g. the development). Good security requirements can have a massive impact on security and are therefore not less important than other requirements.
Application Security Standards
Security requirements are also important to ensure compliance to internal and external requirements such as PCI DSS, DSGVO, BDSG, OWASP, and BSI.
Especially for large companies we recommend the implementation of a comprehensive technical security standard for application and Web security and to derive implementation-specific secure coding guidelines from it. We’ve published TSS-WEB, a template for such a standard, that you can use for free as a foundation or orientation to implement your own.
This approach is illustrated by the following figure:
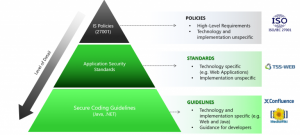
In addition to such technical requirements, the specification of technical security requirements is of course also important. There are a number of very useful methods, such as Evil User Stories or Abuse Cases, which can be also used very well integrated into agile software development.
Secure Coding Guidelines
We at Secodis have developed extensive practical know-how in this field, especially for the Java stack and for various Web frameworks. If you need sound requirements or guidelines we do not start in a “green-field” but can use our existing security guidelines as a comprehensive foundation for your customization. This approach is not only cost-effective but ensures a high quality of your requirements as well. Since many customers prefer to build their guidelines within Atlassian Confluence, we provide our content as Confluence export as well. Integration into SharePoint (via SharePoint Connector) is possible as well.
The following screenshot shows the standard landing page of our guidelines that you customize to your own needs of course:
Our current security content consists of the following modules:
- Threat Catalog: Consits of common threats (currently > 60) to Web-based applications with references to OWSP OWASP Top Ten, OWASP Guidelines, CAPEC and CWE.
- Secure Coding Guidelines: Consists of security guidelines (currently > 48) that are derived from the threat catalog with references to relevant OWASP content and which includes comprehensive implementation notes (including code snippets) for various programming langugages and frameworks, such as:
- Java EE
- Java-EE-Frameworks JSF, GWT and Spring MVC/Security
- JavaScript & HTML5
- Angular / AngularJS
- Node.js
- C#, ASP.NET and ASP.NET Core
- Threat Modeling Template: Allows you to create own threat modelles in Confluence based on a cusstomizable questionaire and our threat catalog
- Web Security Policies: As a plus you can also get the Conflucence content of our Web Security Standard TSS-WEB (https://tss-web.secodis.com), that you can use to create your own policies.
- Available in English only.
Of course, we can customize the content to your specific needs:
- Integration of requirements for additional languages, technologies and frameworks that are not covered.
- Integration of specific security requirements of customer (e.g. use of security gateway).
- Execution of internal developer trainings based on these guidelines
- We can also update your custom content